
Advertisers tricked into believing that they were buying OTT/CTV ads; CBS News, Fox, PBS among premium Roku publishers victimized by app spoofing
Grindr, a dating app popular in the LGBTQ community and owned by Chinese gaming company Kunlun Tech, was utilized in an apparent cross-device ad fraud scheme that tricked advertisers into thinking they were buying video advertisements on Roku connected TV devices, according to new research from Pixalate.
The apparent scheme, which Pixalate has named “DiCaprio,” reveals how scammers can abuse security loopholes that exist in mobile app advertising to carry out ad fraud attacks spanning multiple devices, including the lucrative OTT/CTV ad ecosystem.
Grindr — which has been downloaded from the Google Play Store over 10 million times and is a “social networking app for gay, bi, trans, and queer people" — was the platform through which the fraudsters initiated the apparent scam.
In short, Grindr was apparently weaponized by ad fraudsters, using real people’s devices as proxies to carry out apparent fraud, raising even more questions around app security, consumer privacy, national security, and ad fraud prevention.
Here's how DiCaprio worked:
The DiCaprio "Whitelisted Apps" script contains:
Consisting of 143 unique lines of code, DiCaprio’s ‘Whitelisted Apps’ script — which may have been named in a manner designed to obfuscate the script's actual purpose — generates myriad combinations of the above variables to spoof OTT/CTV app traffic.
CBS News, Fox, PBS, USA Today, and TMZ were among the premium publishers that were spoofed as part of this apparent scheme.
You can download the full list of spoofed apps. These apps are among the victims of the DiCaprio scheme.
The top eight apps (based on Roku ratings in DiCaprio’s "Whitelisted Apps" script) are shown below:
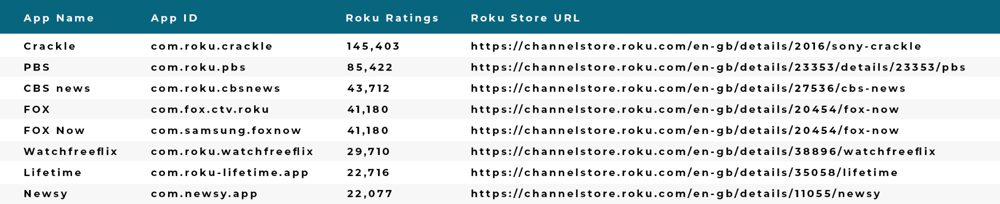
As detailed in Pixalate’s video, the information contained in the fabricated ad requests came from the DiCaprio script, which was hosted on alefcdn.com. The scripts appear to have been exclusively designed to spoof OTT/CTV traffic coming from Roku apps on Roku devices.
There are three components to the DiCaprio script as it relates to the Roku spoofing via Grindr:
Note: The DiCaprio scripts were hosted on alefcdn.com, but the scripts were taken down last week, shortly after BuzzFeed News launched its own investigation. We have linked to archived versions of the scripts.
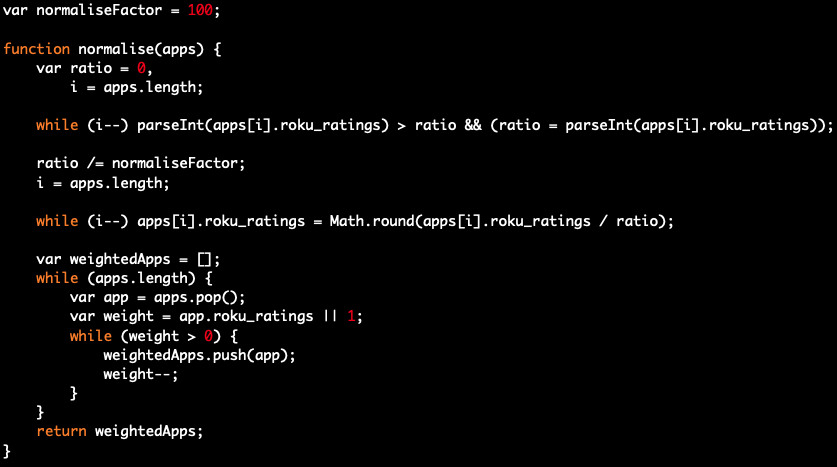
In an apparent bid to make the spoofed traffic appear more legitimate, the alleged scammers behind DiCaprio wrote several lines of code (shown below) to determine how often certain Roku apps should be spoofed without unduly risking detection.
The DiCaprio script used real Roku ratings as a proxy for how “popular” a given app is. An app's popularity was then blended into the algorithm so that the fabricated traffic patterns were realistically weighted. See the screenshot below for details:
While the spoofed impressions always appeared to come from a Roku device, the actual model of the fake device would rotate.
The Supported Devices arm of the DiCaprio script (see below) contained a list of 11 different unique Roku devices that were cycled through randomly as part of the spoofing. See the screenshot below for details:
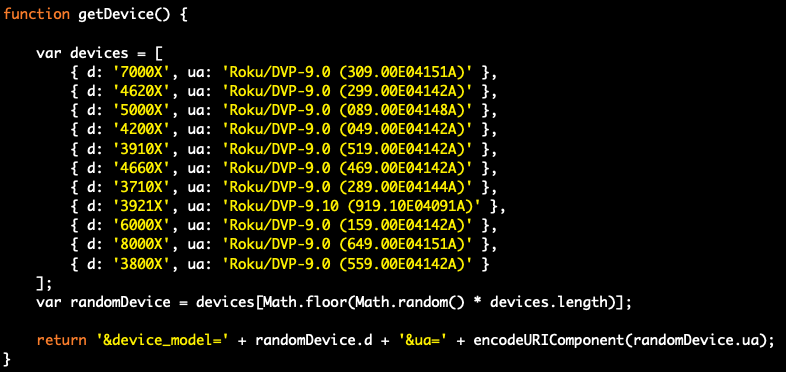
Other elements of the DiCaprio script were hard-coded, including the spoofed device (Roku) and spoofed screen size (1920x1080).
Watch Pixalate’s full video for additional details regarding the mechanics of the apparent scheme.
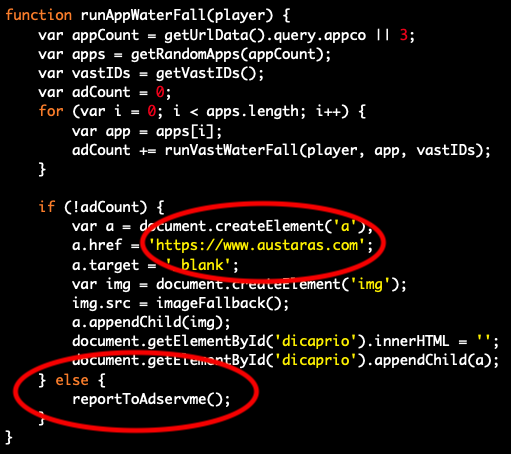
The DiCaprio script contains fallback coding in the event its JavaScript fails to assemble a valid ad request. As shown in the above screenshot, if this occurs, the script generates a blank element with an a.href of austaras.com.
If a valid ad request is assembled, then the script runs a function called “reportToAdservme,” which sends a beacon — in this case, a conversion tracking event — to rtb.adservme.com. This is possibly done to maintain a ledger of events for billing purposes.
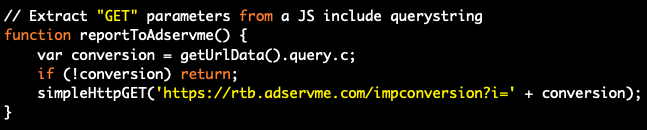
As noted above, the DiCaprio script contains a fallback which refers to Austaras, and a conversion tracking event that refers to AdservME. Here is more information about those two companies:
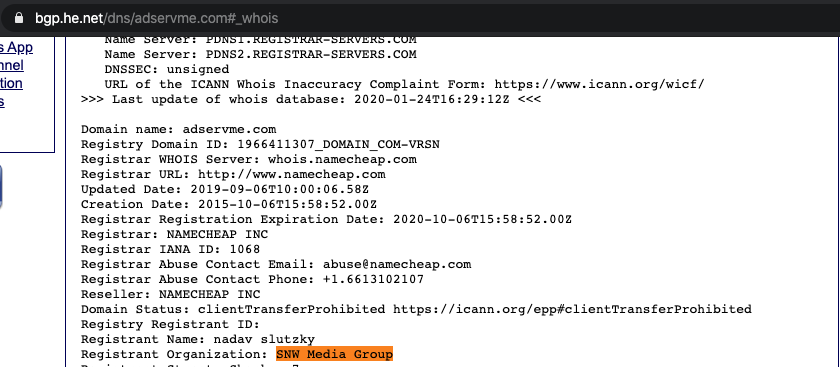
Austaras appears to be a Hawaiian jewelry store. According to public Whois data, Austaras was registered under the organization “SNW” and under the name “Nadav Slutzky,” which is the same name as the CEO of S&W Media Group.
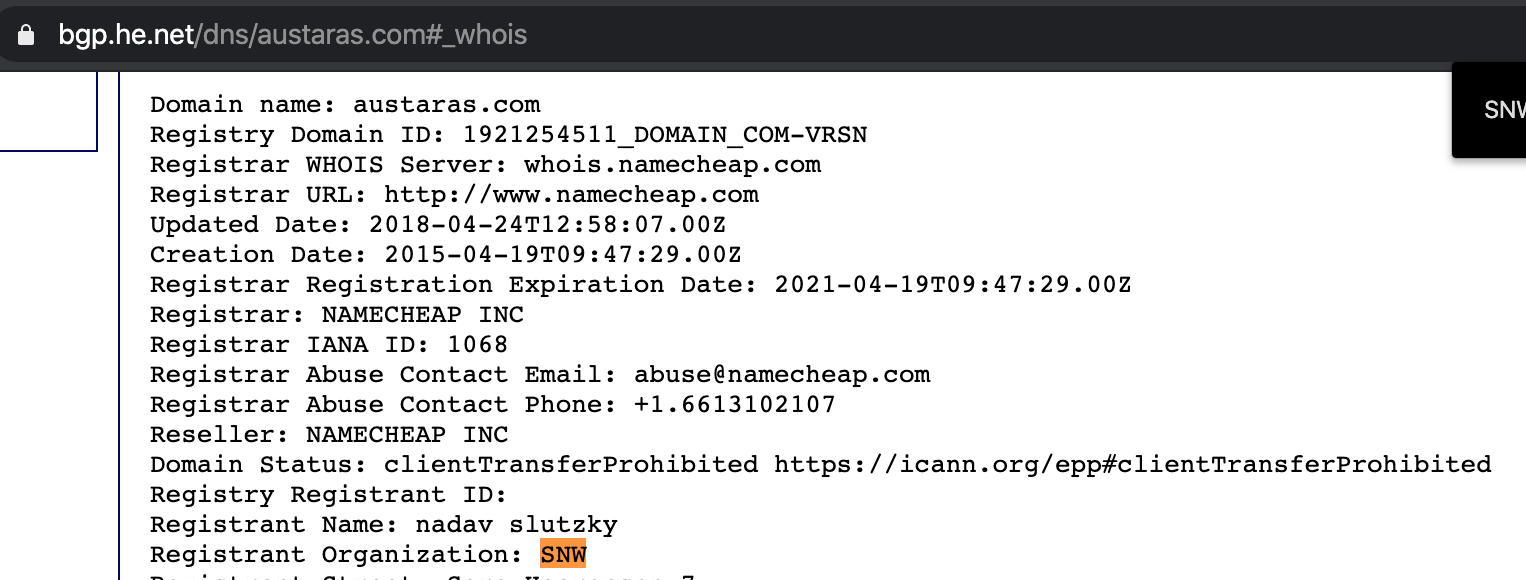
Adservme.com — which now redirects to adservme.co — claims to be a real-time bidding (RTB) exchange. According to public Whois data, adservme.com was registered under the organization “SNW Media Group.” “Nadav Slutzky” is also the registrant name on this domain, and he is also listed as the CEO of AdservME.
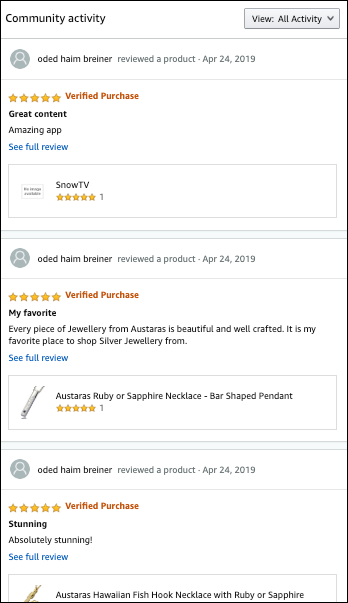
Austaras also sells its jewelry through Amazon. One reviewer by the name of “Oded Haim Breiner" — the same name as S&W Media Group’s CTO — left four Amazon reviews on April 24, 2019: Three on Austaras jewelry pieces and one on the SnowTV app, which is owned by S&W Media Group.
Pixalate is sharing these insights not to assert or assign culpability, but because it is our opinion that our readers will be interested in learning more about possible ties between Austaras, AdservME, and S&W Media Group.
As noted above, Pixalate’s research team discovered that the DiCaprio “R Player” was the primary script used in the apparent Grindr scheme, and it pulled data from DiCaprio's “Whitelisted Apps” and “Support Devices” scripts.
However, Pixalate’s team also discovered other DiCaprio scripts, though the additional scripts did not appear to be utilized in the apparent Grindr scheme.
Our research team also uncovered a DiCaprio “G Player," which is identical to the “R Player" save for the video ad platform hardcoded into the script.
While “R Player" appears to have been created to spoof ad requests using the SpringServe platform, “G Player" appears to have been created to use the Streamrail platform.
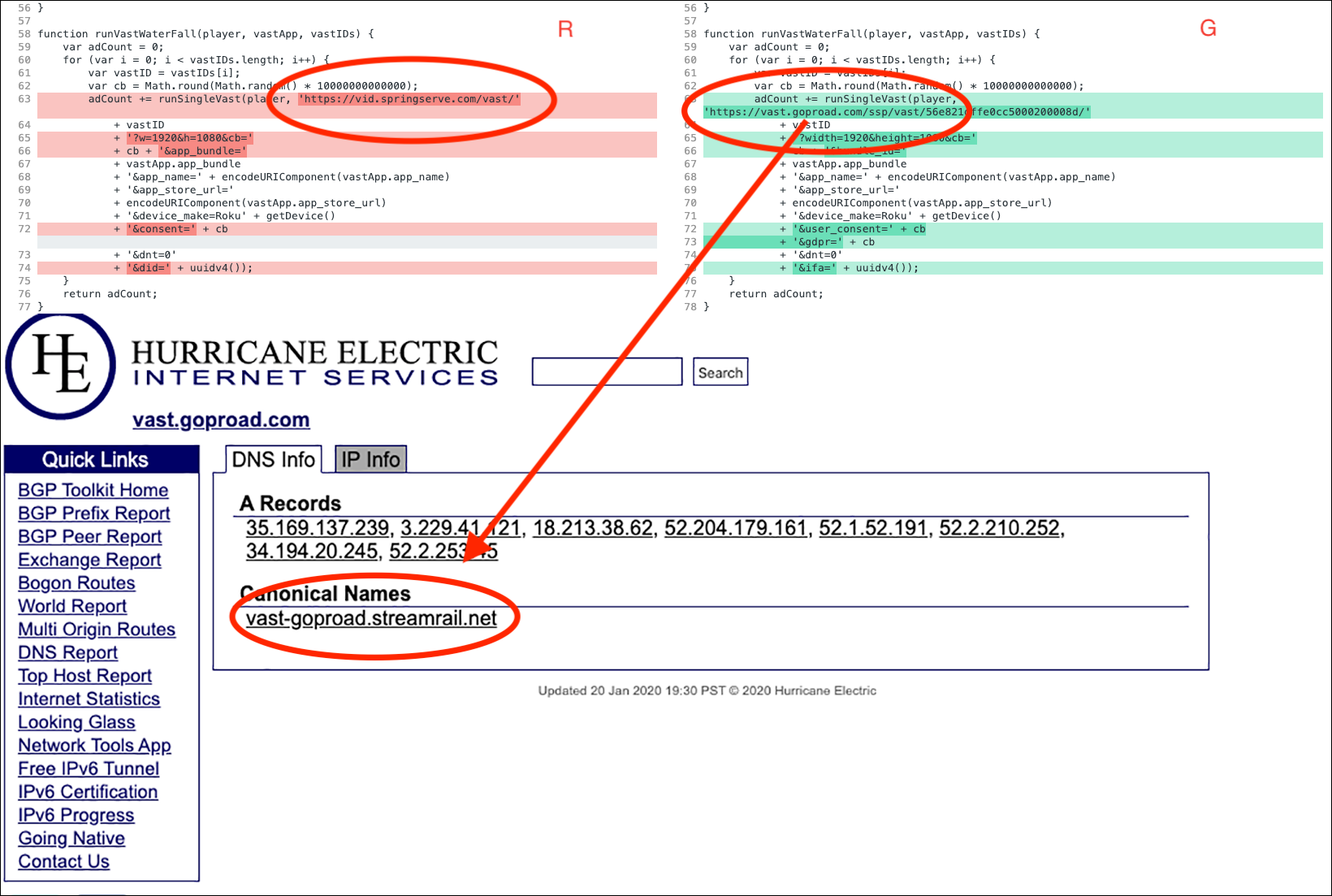
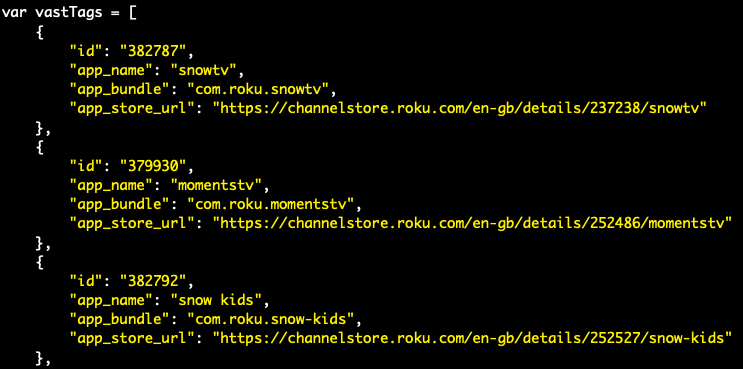
Pixalate's research team also uncovered a DiCaprio “Player” script, which is similar to the “R” and “G” Players, except it does not reference the “Supported Devices” or “Whitelisted Apps” scripts. Instead, the “Player” script has a self-contained list of Roku apps.
The “Player” script has 15 Roku apps listed — 14 of which belong to S&W Media Group. Here’s a sample:
While Pixalate was able to verify the deployment of the DiCaprio script via the Grindr app on Android devices, all DiCaprio scripts uncovered are OS agnostic, meaning it appears to have been designed to be capable of creating fraudulent traffic from both iOS- and Android-powered mobile devices.
Additionally, as shown through our discovery of both the “G” and “R” Players, DiCaprio’s scripts are flexible and easily transferable from platform to platform.
By weaponizing real, popular mobile apps, fraudsters are now capable of turning consumers into fraud vectors.
Not only does this help scammers scale with minimal cost — in DiCaprio, for example, over 10 million consumer devices had the potential to be used as free server space — but it also compounds concerns over safety in the mobile app economy, including brand safety, ad fraud prevention, consumer privacy, and national security.
According to the New York Times, citing research from the Norwegian Consumer Council, Grindr, along with other popular dating services, "are spreading user information like dating choices and precise location to advertising and marketing companies in ways that may violate privacy laws."
Pixalate’s DiCaprio discovery, which utilized Chinese-owned Grindr, also comes amid concerns over foreign-owned apps, including popular apps from China such as TikTok. Some foreign apps are considered national security threats by the U.S. government, and all examples of data malpractice are more closely scrutinized.
Disclaimer
The content of this blog posting reflects Pixalate’s opinions with respect to, among other things: (i) its apparent discovery of an OTT/CTV ad fraud scheme; (ii) the elements of any such purported scheme(s); (iii) parties, brands, platforms, and apps that may have benefitted from, participated in, or been exploited or victimized by such alleged scheme(s); and (iv) other factors, information, and observations that Pixalate believes may be useful to the digital media industry. Any proprietary data shared is grounded in Pixalate’s proprietary technology and analytics, which Pixalate is continuously evaluating and updating. Any references to outside sources should not be construed as endorsements. Pixalate’s opinions are just that, opinions, which means that they are neither facts nor guarantees.
Per the MRC, “'Fraud' is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes. Also per the MRC, “‘Invalid Traffic’ is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”
It is important to also note that Pixalate’s references to the possible role(s) of certain parties, brands, platforms and apps in connection with this apparent scheme are not intended to assert or imply, conclusively or otherwise, that such parties, brands, platforms, and apps were in any way beneficiaries of, participants in, or knowledgeable regarding this apparent scheme. Nor were such references intended to assert or assign culpability for any possible intentional or negligent conduct.
Finally, brands, logos, and trademarks specified in this blog posting and related media are utilized merely for referential purposes, and such brands, logos, and trademarks remain the property of their respective registrants and owners, as applicable.
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.
These Stories on Mobile
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.

Disclaimer: The content of this page reflects Pixalate’s opinions with respect to the factors that Pixalate believes can be useful to the digital media industry. Any proprietary data shared is grounded in Pixalate’s proprietary technology and analytics, which Pixalate is continuously evaluating and updating. Any references to outside sources should not be construed as endorsements. Pixalate’s opinions are just that - opinion, not facts or guarantees.
Per the MRC, “'Fraud' is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes. Also per the MRC, “‘Invalid Traffic’ is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”

