BuzzFeed News has investigated, expanded, and possibly identified a ring of bad actors related to Pixalate’s MegaCast mobile app laundering discovery. Their extensive investigation demonstrates a clear example of the sophisticated ends taken by companies intent on fraudulently profiting from mobile app advertising. The apparent scheme — involving app acquisitions by shell companies, fake emails and websites, and advanced malware — underscores the risky nature of the mobile in-app advertising landscape.
BuzzFeed was alerted to the ad fraud scheme through Pixalate’s initial discovery, and used our findings as a foundation for their detailed inquiry. “The scheme began to unravel this summer when data scientists at Pixalate detected something alarming in an Android app called MegaCast,” wrote BuzzFeed. “The app’s pitch was that it enabled a user to play any video, regardless of format, on a streaming device. But behind the scenes, MegaCast was pretending to be something it wasn’t.”
Over the past several months, Pixalate worked alongside BuzzFeed to help them better understand the MegaCast discovery and ad fraud within mobile apps. BuzzFeed News also conducted its own thorough investigation into the alleged scheme and uncovered new facts within the unsettled mobile app environment.
Through ongoing research, Pixalate has discovered that over 11 million individual devices were potentially impacted by the alleged MegaCast ad fraud scheme, adding risk not only to the reputation of the brands involved but also to the consumer devices themselves.
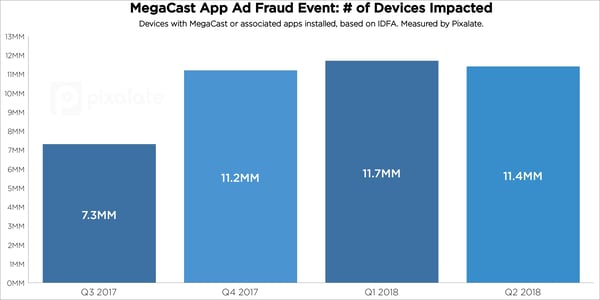
Using our global data intelligence, we conducted a quarterly analysis over the past year to see the number of devices, based on IDFA*, that had either MegaCast or any of the associated apps installed.
BuzzFeed says it identified parties behind the ‘massive ad fraud scheme’
BuzzFeed took Pixalate’s findings and pursued the bad actors at the source of the fraud scheme. BuzzFeed’s investigation found that “seemingly separate apps and companies are today part of a massive, sophisticated digital advertising fraud scheme involving more than 125 Android apps and websites connected to a network of front and shell companies in Cyprus, Malta, British Virgin Islands, Croatia, Bulgaria, and elsewhere.”
BuzzFeed traced “corporate records, domain registration information, DNS data, and other publicly available sources … [which] led to [a] group of four men operating Fly Apps, which owns MegaCast, EverythingMe, and other applications.”
“One way the fraudsters find apps for their scheme is to acquire legitimate apps through We Purchase Apps and transfer them to shell companies,” reported BuzzFeed. “They then capture the behavior of the app’s human users and program a vast network of bots to mimic it.”
Pixalate regularly works with companies interested in preventing ad fraud and making the programmatic ecosystem more secure. We were pleased that BuzzFeed unearthed further significant findings and are adding any newly identified fraud sources to our detection and filtration products, including Pixalate’s pre-bid blocklists.
New: Pixalate reveals the scheme grew by 53% in Q4 2017
The total number of devices with any of the suspicious apps exploded in Q4 2017, potentially to exploit holiday budgets. As the chart above shows, the number of impacted devices rose 53% from Q3 to Q4 2017, leveling off above 11 million during the first half of 2017.
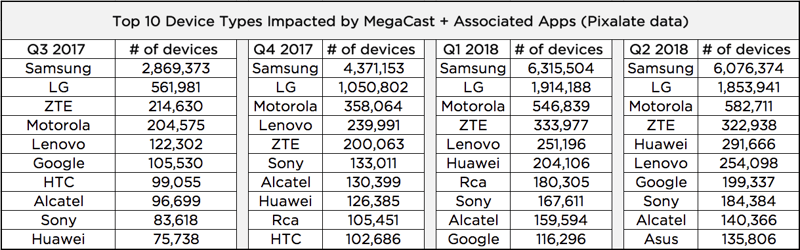
We also analyzed the individual device types that were hit the hardest. Based on our data, Samsung device users were impacted by the apps in question the most.
Pixalate’s initial MegaCast mobile app laundering discovery
In June 2018, Pixalate published a blog highlighting what we believed to be a significant example of mobile app laundering. We detailed how the MegaCast - Chromecast Player application — which had been downloaded over 1 million times at the time of our discovery — appeared to spoof dozens of other mobile apps as part of an elaborate laundering scheme.
Based on our conservative estimates, the MegaCast mobile app laundering activity was costing advertisers tens of millions of dollars per year.
Facebook, Disney among brands impacted by this mobile app ad fraud
In July, we conducted follow-up research into the MegaCast mobile app laundering activity and built a partial list of companies that we believe were victimized by the scheme.
Given the magnitude of this mobile app ad fraud activity, a large number of brands were impacted. Based on our additional research, Pixalate was able to identify and verify some of the exact brands we believe were impacted, including Facebook, Disney, Instagram, Hulu, Volvo, Ram Trucks, L’Oreal, Lyft, Marvel, and more.
For a more complete list of the brands we believe were impacted, download our free whitepaper that shares network capture images as well as images of the creatives.
See the mobile app ad fraud in action
Pixalate’s data analysis team captured video evidence of the mobile app laundering, which was carried out via Bundle ID spoofing.
This video shows what can go on behind the scenes during an ad fraud attack.








