Pixalate has uncovered a family of web sites committing session hijacking — a form of Sophisticated Invalid Traffic (SIVT), as defined by the MRC. The sites in question are capable of hijacking a user’s browser without any malware installed, continually refreshing the browser to generate more ad revenue. (Update: The sites in question appear to have been taken down. But this post still contains video and data to detail how this type of attack works.)
The “zombie sites” work on both desktop and mobile devices. On mobile devices, the site attempts to pull users away to the App Store.
Monkey Frog Media is the parent site and home to a number of sites that all commit the same type of ad fraud. It claims to be a site dedicated to three topics — food, parenting, and technology — but it appears to be a front to commit ad fraud. The sites under Monkey Frog Media’s umbrella include:
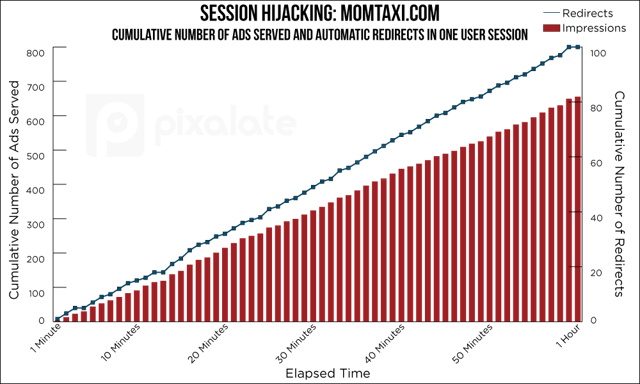
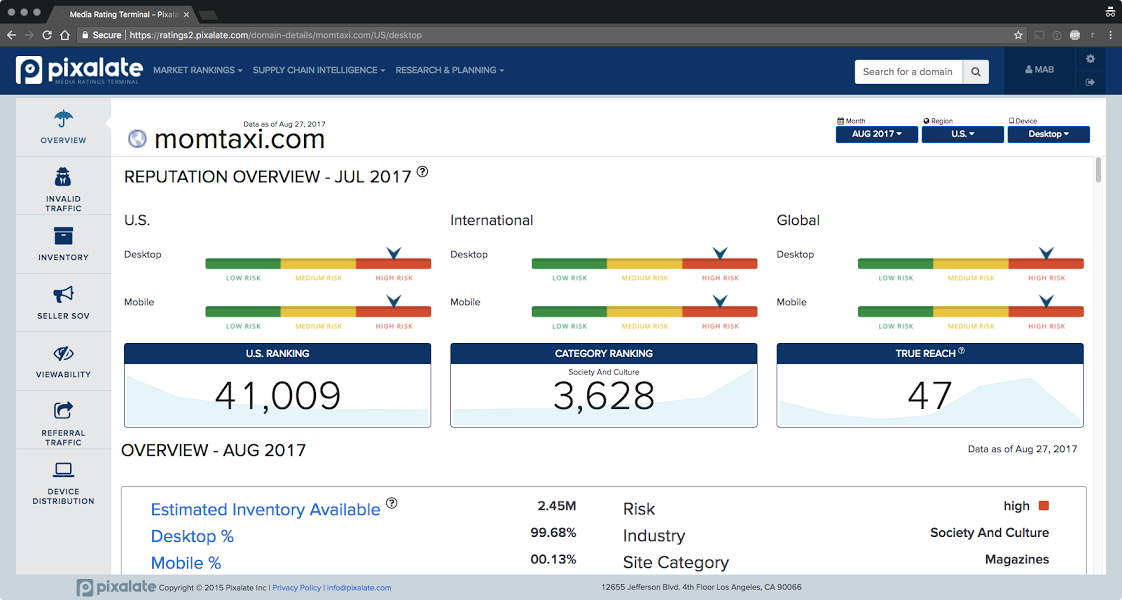
The cumulative effect of a hijacked web browser can be devastating for advertisers. In our analysis of MomTaxi.com, using the Chrome browser, after just 10 minutes, nearly 100 ad impressions will be served to a single “user.” All of this data shows just one user session within a single browser.
This attack is unique because it does not just auto-refresh the page to generate more impressions, like many similar session hijackings. This threat also self-navigates to replicate legitimate human activity.
This is a sophisticated attack that linearly spaces automatic redirects to mimic real user behavior. The correlation between redirects and elapsed time has a nearly perfect R-squared, of .999. The fraud attack leads to a tidy 100 internal redirects per hour — or about 5 redirects every 3 minutes.
The Monkey Fraud Media ad fraud ring is also sophisticated in that its technology is capable of identifying which browser or device the "user" is on. The attack uses this data to inform its redirects.
For example, the websites make calls to the Apple store. If you were on an iTunes-compatible device, the site will automatically navigate you to the iTunes store through a series of malicious redirects (that likely give the fraudster referral credit).
Depending on which browser or device you are using, the attack can attempt to drive you off of the site to another site, again through a series of malicious redirects.
These sites also auto navigate and refresh within different tabs and browsers, even if you don’t have the tab or browser open. This allows the fraudster to exponentially multiply the attack and the amount of money stolen.
According to our data, the estimated price paid for ads on Mom Taxi is $0.75 CPM. Based on all of this data, if the fraudster were able to keep 2,000 browsers/tabs open on Mom Taxi all day (via a farm, for example), then they would steal nearly $25,000 per day from advertisers.
To be clear: These figures represent hypothetical scenarios that depict how this site — or similar sites/attacks — could impact marketers’ pocketbooks. Even if we take one of the more modest hypotheticals (500 browsers/tabs left open for 24 hours), a sustained attack would net the fraudsters over $2 million per year.
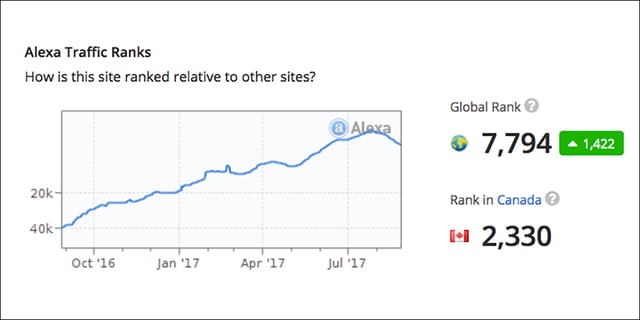
You may not have ever heard of Monkey Frog Media or its subsidiary sites, but the site has catapulted up the Alexa rankings in recent months.
As of this writing, monkeyfrogmedia.com ranks #2,330 in Canada and #7,794 globally. In September of 2016, it wasn’t even in the top 40,000.
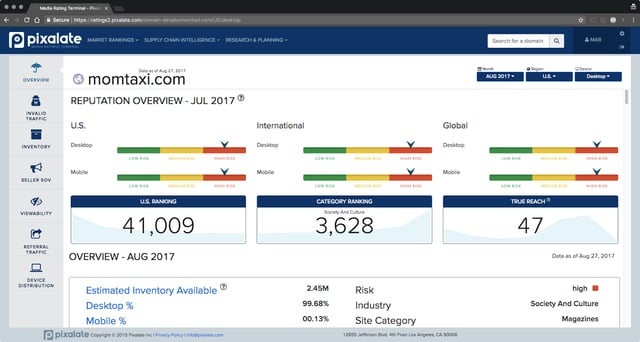 The Pixalate Media Rating Terminal (MRT) shows that MomTaxi.com is a high-risk site for both desktop and mobile ad impressions.
The Pixalate Media Rating Terminal (MRT) shows that MomTaxi.com is a high-risk site for both desktop and mobile ad impressions.
Interestingly, while Monkey Frog Media has seen a meteoric rise in its Alexa rankings, none of its subsidiary sites have dramatically improved, according to their individual rankings. By looking at the SimilarWeb information, we can see that 100% of this site's traffic goes to "click.monkeyfrogmedia.com," and each of the individual properties has "click.monkeyfrogmedia.com" as a top referral traffic source. This referral loop boosts Monkey Frog Media’s rankings, making it appear legitimate.
Looking at the SimilarWeb information once again, one can see that the top sources of inbound referral traffic are porn or illegal streaming sites for each individual property.
Want more data-driven insights? Sign up for our blog!
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.
These Stories on Thought Leadership
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.

Disclaimer: The content of this page reflects Pixalate’s opinions with respect to the factors that Pixalate believes can be useful to the digital media industry. Any proprietary data shared is grounded in Pixalate’s proprietary technology and analytics, which Pixalate is continuously evaluating and updating. Any references to outside sources should not be construed as endorsements. Pixalate’s opinions are just that - opinion, not facts or guarantees.
Per the MRC, “'Fraud' is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes. Also per the MRC, “‘Invalid Traffic’ is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”

