
Roku apps designed for passive viewing appear to have been targeted in a new over-the-top (OTT) content and connected TV (CTV) ad fraud scheme unearthed by Pixalate researchers.
The alleged ad fraud scheme exploited over a dozen Roku apps in an apparent scheme that looks to have exploited OTT/CTV advertisers including political ad groups, luxury automakers, and CPGs.
This alleged scam is unique in the fact that the spoofing appears to originate on actual OTT/CTV devices and apps — in this case, Roku devices and apps — rather than originating on a mobile device, such as was the case in our DiCaprio discovery.
Adweek has additional coverage on "Monarch."
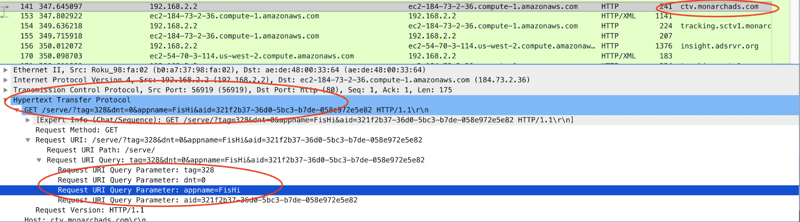
Request:
Response:
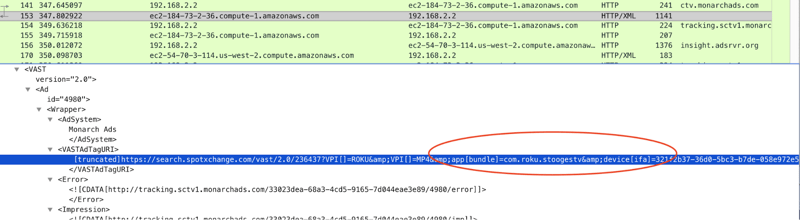
In short: Screensaver-like Roku apps that use Monarch Ads’ platform seek to fill their inventory. However, app spoofing occurs, and the spoofed apps all purport to belong to a developer named Aragon Creek. Monarch Ads is a subsidiary of Barons Media, and Aragon Creek appears to be owned by the owner of Barons Media.
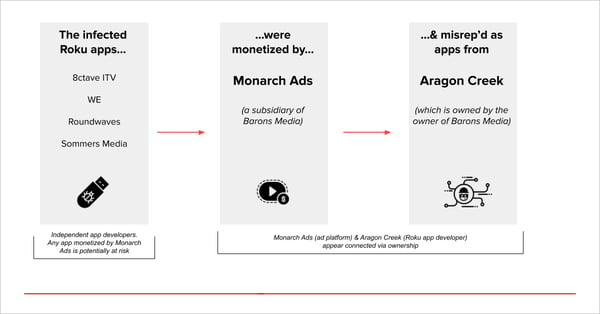
Pixalate is sharing these insights not to assert or assign culpability, but because it is our opinion that our readers may be interested in learning more about possible ties between Monarch Ads, Barons Media, and Aragon Creek.
Pixalate has observed the spoofing activity across over a dozen apps from at least four different app developers. The structure of the apparent scheme is the same on all apps observed.
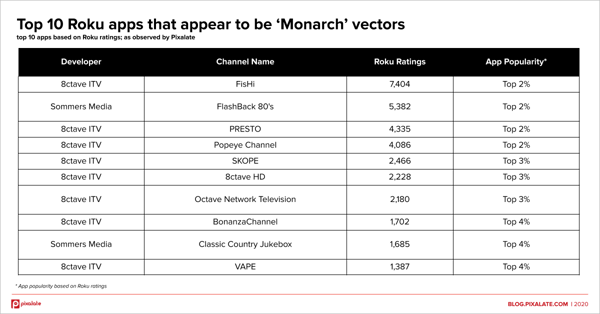
The 10 most popular apps (based on Roku ratings) that appear to be vectors for the alleged “Monarch” fraud are:
Developers/apps utilized in the scheme included but were not necessarily limited to:
All of the top 10 apps listed above are among the 4% most popular apps on the Roku Channel Store, using store ratings as a proxy for popularity.

Brands that appear to have been impacted include, but are not limited to:
Several political groups and political campaigns appear to have also been duped by the apparent scheme, including but not limited to:
Download the PDF containing screenshots of creatives captured by the Pixalate research team, including additional brands and political organizations that appear to have been impacted.
Ad platforms that appear to have been impacted include, but are not necessarily limited to:
In the data observed by Pixalate, all of the above platforms were fed, or inherited, spoofed bid parameters. The spoofed bid parameters appear to have come either directly from, or down the chain from, Monarch Ads.
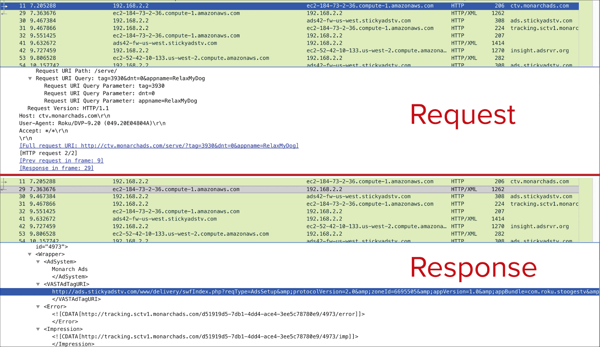
Example: Spoofed bid parameters fed directly to a platform
Below is an example of a platform apparently being fed spoofed bid parameters from Monarch Ads.
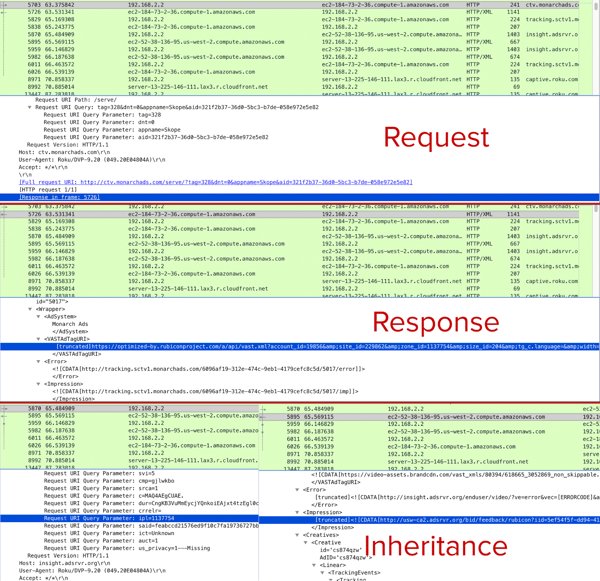
Example: Spoofed bid parameters inherited by a platform
Below is an example of a platform apparently inheriting spoofed bid parameters down the line from Monarch Ads.
The apps used in the scam have screensaver-like effects — such as a digital aquarium — or content designed for pets, such as “relaxing music for cats.” One of the channels is designed, in part, to be a “pet-sitter for the times you are out of the house."
These apps are not labeled as “screensavers” on Roku’s platform because their content is labeled as “special interest” instead. In the context of the “Monarch” scam, this distinction appears to be important for two key reasons (per Roku’s developer documentation):
By avoiding the Roku label of “screensaver” — while still having screensaver-like functionality, a passive viewing experience, or a viewing experience not even intended for humans — an exploited app would be able to serve video ads, which could make them a perfect target for the “Monarch” scheme.
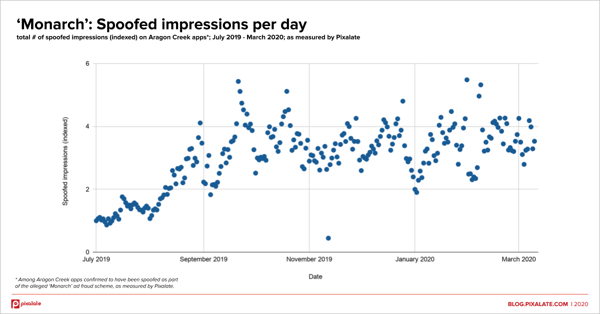
Using conservative estimates, these unattended apps appear to have been used to generate hundreds of thousands of invalid traffic (IVT) impressions per day for over six consecutive months.
The spoofed apps (the Aragon Creek apps) feature content consisting of old TV shows and movies that may have entered the public domain, such as episodes of the Three Stooges, Roy Rogers, The Andy Griffith Show, and more.
Aragon Creek appears to have over 60 Roku apps. And because the content on these channels is traditionally “brand-safe,” it can command a higher CPM than something like a screensaver or a channel for dogs.
The apparent scammers nearly tripled the daily spend siphoned from July to September 2019 with high-value inventory of roughly $25 CPM, using industry standards as a baseline.
The money lost per day to this alleged scam then suddenly stopped increasing and remained consistent for the next seven months. The scheme appears to still be active as of March 2020.
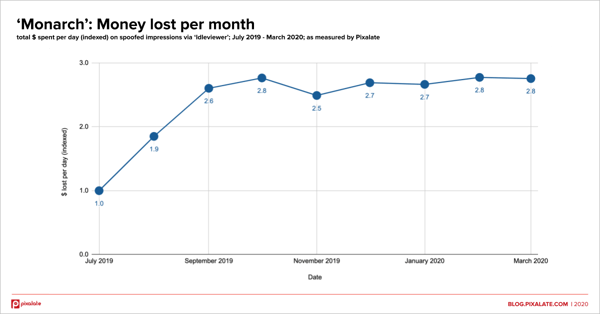
By digging into the data of this apparent fraud scheme, Pixalate sees characteristics consistent with device farms.
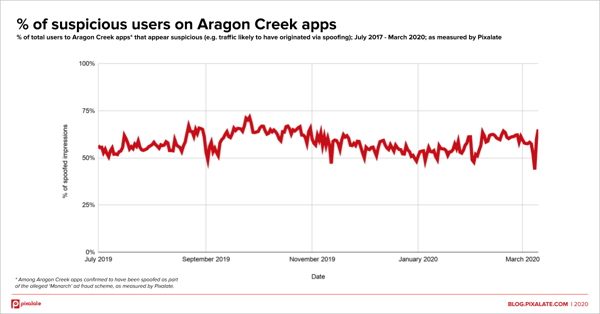
The chart below shows the total number of suspicious users of Aragon Creek apps (among apps confirmed to have been spoofed as part of the scheme):
And below is a chart examining suspicious impressions, i.e. the percentage of all impressions that were delivered to suspicious users:
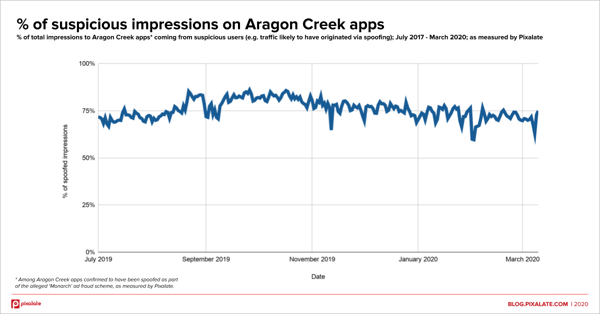
Additionally, the suspicious-user to suspicious-impression ratio is also in line with what one might see coming from a device farm.
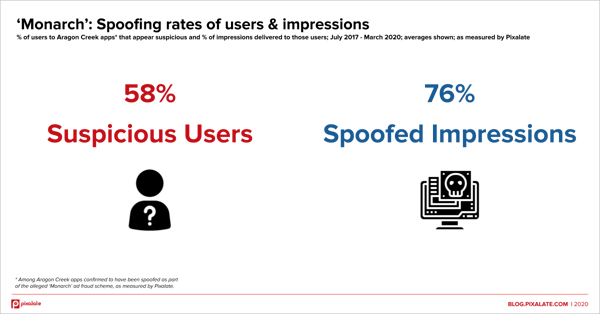
On average, 58% of the users watching the Aragon Creek apps in question have strong spoofing signals. Those 58% of users account for 76% of the impressions.
As revealed by Pixalate’s two recent OTT/CTV ad fraud discoveries — “DiCaprio” and “Monarch” — scammers appear to be ramping up their efforts in the burgeoning OTT/CTV ad space.
Additionally, the “Monarch” discovery shows that no intermediary device (e.g. a phone or computer) is required to carry out OTT/CTV ad fraud attacks. Scammers have devised ways to apparently steal these lucrative ad dollars directly from actual OTT/CTV devices.
2020 is an election year, and the “Monarch” discovery appears to show that political ads may have already fallen prey to OTT/CTV ad scams, including ads from politicians, committees, advocacy groups, and more. And these are ads coming from groups with powerful backers, such as the Chan Zuckerberg Initiative, or the Governor of California.
Ad fraudsters are zeroing in on all aspects of the OTT/CTV ad ecosystem, drawn by the explosive growth and high CPMs.
Disclaimer
The content of this blog posting reflects Pixalate’s opinions with respect to, among other things: (i) its apparent discovery of an OTT/CTV ad fraud scheme; (ii) the elements of any such purported scheme(s); (iii) parties, brands, platforms, and apps that may have benefitted from, participated in, or been exploited or victimized by such alleged scheme(s); and (iv) other factors, information, and observations that Pixalate believes may be useful to the digital media industry. Any proprietary data shared is grounded in Pixalate’s proprietary technology and analytics, which Pixalate is continuously evaluating and updating. Any references to outside sources should not be construed as endorsements. Pixalate’s opinions are just that, opinions, which means that they are neither facts nor guarantees.
Per the MRC, “'Fraud' is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes. Also per the MRC, “‘Invalid Traffic’ is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”
It is important to also note that Pixalate’s references to the possible role(s) of certain parties, brands, platforms and apps in connection with this apparent scheme are not intended to assert or imply, conclusively or otherwise, that such parties, brands, platforms, and apps were in any way beneficiaries of, participants in, or knowledgeable regarding this apparent scheme. Nor were such references intended to assert or assign culpability for any possible intentional or negligent conduct.
Finally, brands, logos, and trademarks specified in this blog posting and related media are utilized merely for referential purposes, and such brands, logos, and trademarks remain the property of their respective registrants and owners, as applicable.
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.
These Stories on CTV
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.

Disclaimer: The content of this page reflects Pixalate’s opinions with respect to the factors that Pixalate believes can be useful to the digital media industry. Any proprietary data shared is grounded in Pixalate’s proprietary technology and analytics, which Pixalate is continuously evaluating and updating. Any references to outside sources should not be construed as endorsements. Pixalate’s opinions are just that - opinion, not facts or guarantees.
Per the MRC, “'Fraud' is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes. Also per the MRC, “‘Invalid Traffic’ is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”

